Hack The Box - Resolute
Working on another machine using the Hack The Box service and was able to quickly get user Resolute.
The place to start is to perform an always is reconnaissance. Running an NMAP scan against the server reveled that this server had LDAP installed.
sudo nmap -sS 10.10.10.169
We can continue our reconnaissance phase and scan the server's LDAP information with enum4linux.pl.
Running the following command ./enum4linux.pl -a 10.10.10.169 returned some interesting results. This returned an account with a description with a password in it.

Marko Novak has a description of a password being set to Welcome123! I noticed WinRM is enabled. Lets try logging into the system as Marko using EvilWinRM.
evil-winrm -i 10.10.10.169 -u marko -p Welcome123! cmd
It appears that Marko's password is no longer Welcome123!. Lets try that password using[...]
Enabling DNS over TLS On Android
Android version Pie 9 has a new feature called Private DNS that allows you to permanently force the DNS to a secure DNS provider. If you are not on Android version 9 or newer there may be apps that allow you to accomplish the same thing.
DNS over TLS versus DNS over HTTPs
The biggest difference between DNS over TLS and DNS over HTTPS is there is a dedicated port for DNS over TLS, which is 853. This brings in concerns as your DNS queries are unable to hide itself as regular web traffic.
There are arguments against DNS over HTTPS in that it is harder for network administrators to monitor DNS traffic. There are tools that help protect organizations by preventing certain domain names being resolved and comparing the domain query names against threat communities.
Enabling Android Private DNS (DNS over TLS)
This is the easiest method to permanently change your DNS settings on Android 9 and newer devices. Navigate to Settings -> Network & Internet- > Advanced. On[...]
Graylog Pipelines - Threat Indicators
Graylog by default provides an included plugin that allows you to check against threat feeds to determine if an IP or an domain has been marked as malicious. This can be expanded on into different areas.
On a fresh install you need to install the content packs in order for the threat intelligence plugin to work. Navigate to System -> Content Packs and click the Install button.
After a few minutes and a refresh of the page there will be a green button that indicates that they have been installed.
Pipelines allow you to modify incoming logs by adding fields, dropping the log and provide additional capabilities via functions. You can get to the pipeline system by going to System -> Pipeline.
Below is a rule that will take a log that has a field of winlogbeat_event_data_QueryName and query the content packs for any reports on it being malicious.
rule "Domain Name Threat Lookup"
when
has_field("winlogbeat_event_data_QueryName")
then
// Lets lookup the OTX [...]
AI Crimes are a thing
We live in an fascinating era, where technology is solving problems that we wouldn’t have thought was possible before. Helping the blind see(https://www.youtube.com/watch?v=y5bktGGkd9w), helping individual’s with Parkinson’s(https://www.youtube.com/watch?v=R6rAlFYDffQ) and more. Please feel free to review those two links for some uplifting news.
But with this technology comes opportunities that criminals can take advantage of. Artificial Intelligence, AI, is being used to generate fake images and sound. Criminals are now generating real time audio to sound like other individuals and perform criminal actions. Please review the link below and be cautious of the person you are speaking with on the phone.
<a href="https://www.theverge.com/2019/9/5/20851248/deepfakes-ai-fake-audio-ph[...]
Sysmon 10 & DNS Queries
On June 19th Mark Russinovich tweeted that the release of Sysmon version 10 will include DNS query logging. Packetbeat is currently being utilized for capturing DNS queries but with the addition of DNS queries in Sysmon this may change.
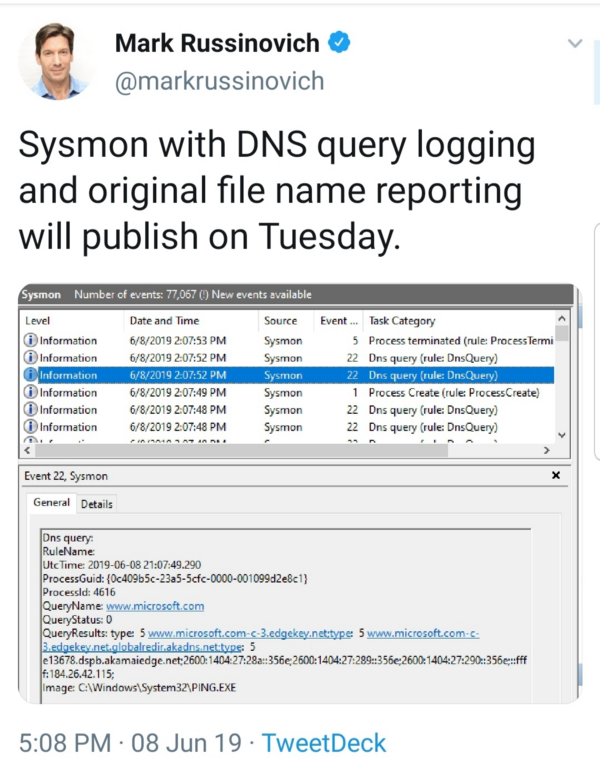
I have started upgrading sysmon in our environment. I am using the base of SwiftOnSecurity’s AlphaVersion for the new configuration file with some changes to fit better in our environment. The Github repository is located here https://github.com/SwiftOnSecurity/sysmon-config. Adding <DnsQuery onmatch=”exclude”/> to your existing configuration file should be enough but highly recommend against this method as it will be extremely noisy.
Currently the logs get shipped to [...]