Threat Hunting with DNS Queries
Majority of malware uses a command and control center to retrieve updates, commands to run and more. There are a few methods that malware can use to obtain the location on where the command and control center can be located.
Using an IP address would limit the command and control center to one location, while a DNS record would allow a system to move around as needed.
Logging the DNS queries will allow you to obtain a baseline of your environment and will allow you to query the domain names against lists of known bad domains.
This document will just go over the very basics of getting the DNS questions into GrayLog.
We will be using Packetbeat to log the queries and will be shipping the information to GrayLog via a LogBeat connector.
In the configuration for Packetbeat you need to specify what interface that will be used for monitoring. Finding the interface you want can be found by Packetbeat devices
Specify what protocols you want to monitor and the settings. You will also need to specify the logstash output.
The Packetbeat configuration below tells the software to monitor on interface 4. The Packbeatbeat.protocols tell the software to watch for DNS traffic and include_authorities The output below send the logs to Logstatsh at graylog.example.com.
packetbeat.interfaces.device: 4
packetbeat.protocols:
- type: dns
# Configure the ports where to listen for DNS traffic. You can disable
# the DNS protocol by commenting out the list of ports.
ports: [53]
# include_authorities controls whether or not the dns.authorities field
# (authority resource records) is added to messages.
include_authorities: true
# include_additionals controls whether or not the dns.additionals field
# (additional resource records) is added to messages.
include_additionals: true
output.logstash:
# The Logstash hosts
hosts: ["graylog.example.com:5048"]
Graylog Configuration
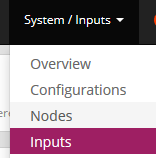
Lets add a Beats Input in GrayLog by navigating to System / Inputs and selecting Inputs.
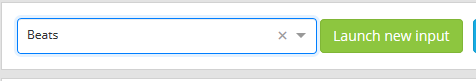
Select Beats in the drop down in the new section and click Launch new Input.
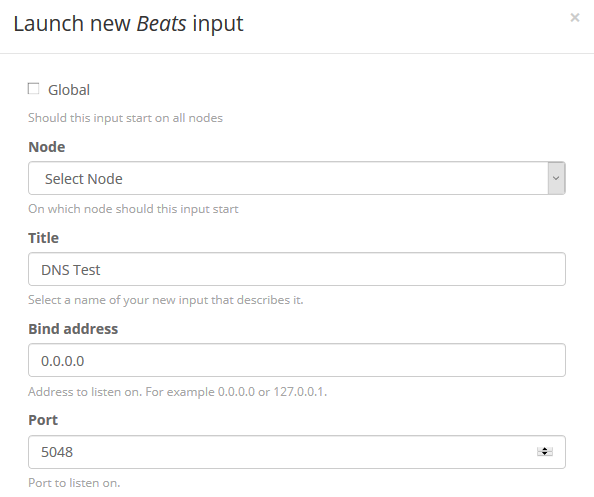
Select the node, title and port.
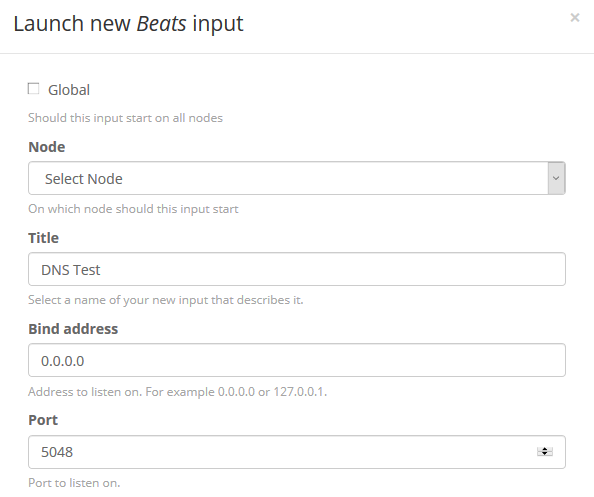
- Start Packetbeat and your DNS queries will start going to GrayLog.
You are now on your way to threat hunting.
Note: I did not cover setting up TLS settings. I would recommend doing this as an additional step.